Are you sure your country's essential ID cards are truly secure? A single forgery can threaten elections and social systems, but understanding the right security features can prevent this national risk.
The essential security requirements for national ID, voter, and social security cards include using custom, non-public materials1, a multi-layered design2, specialized printing processes3, and verifiable features4. Crucially, they must also be tamper-resistant5 and produced in a highly controlled, traceable manufacturing environment6 to prevent fraud.

These cards may look simple, but the security behind them is incredibly complex. In my 15+ years of working with government agencies, I've learned that a document's strength isn't just in one flashy feature, but in a deep, layered strategy. It's a strategy that must be built from the ground up, starting with understanding the immense responsibility these documents carry. Let's break down why this is so important and what goes into making them truly secure, from the initial concept to the final, trusted card.
Why is High Security So Essential for National Identity Documents?
Thinking a fake ID is just a personal problem? It's not. Forged national documents can destabilize governments and compromise entire social systems, affecting every single citizen in the country.
High security is critical because these cards are legal identity documents, not just pieces of plastic. Any forgery poses a direct threat to election legitimacy7, social welfare systems8, and national identity management9, creating a significant risk to the nation's stability and security.
When we talk about a National ID, a Voter Card, or a Social Security Card, we are talking about legal instruments. They are the physical proof of a government's promise to its citizens. They grant rights, provide access to services, and confirm one's place in society. Because of this, the impact of a forgery goes far beyond the individual. I've seen firsthand how governments react when they discover a large-scale forgery operation. The panic is real because it shakes the public's trust in the system itself. A single fake document isn't just one person's problem; it's a crack in the foundation of national security. It creates a ripple effect that can have devastating consequences.
The Ripple Effect of a Single Forgery
The damage caused by a fake document depends on its intended use. Each type of card, when forged, undermines a different pillar of the state. This is why we can't treat them all the same.
| Document Type | Individual Impact | National Impact |
|---|---|---|
| National ID | Identity Theft, Financial Loss | Compromised Borders, Inaccurate Census Data, Terrorism |
| Voter Card | Disenfranchisement of legitimate voters | Illegitimate Election Results, Political Instability |
| Social Security Card | Personal Benefit Theft | Depletion of Social Welfare Funds, System Collapse |
Ultimately, the security of these documents is a direct reflection of a nation's strength and control over its own identity. Protecting them is not an expense; it's a fundamental investment in national stability.
Do Different National Cards Face the Same Security Threats?
You might think all secure cards are made the same way. But a one-size-fits-all security approach leaves dangerous gaps because the threats against each card are completely different.
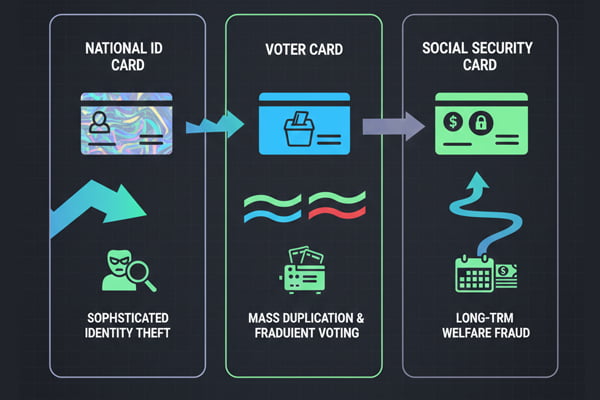
No, they face very different threats. National IDs are targeted for sophisticated identity theft10. Voter cards are attacked to enable fraudulent voting, often through mass duplication11. Social security cards are forged for long-term welfare fraud12. Security must be customized for each specific threat.
In our business, we never start a project by listing features. We start by asking, "Who is going to attack this document, and why?" The motivation of the forger determines their method, and our defense must be tailored to that method. A standardized security template is a recipe for failure because it ignores the unique vulnerabilities of each document. For example, a criminal trying to create a fake ID to cross a border needs a near-perfect, high-quality forgery to pass inspection. But someone trying to rig an election with fake voter cards needs quantity over quality. They might produce thousands of low-quality cards that just need to work once.
A Closer Look at Specific Attack Vectors
Let's examine the different motivations and how they shape the attacks on each card:
-
National ID Cards: The primary threat here is sophisticated identity theft10. Forgers aim to create a document that can pass as genuine for opening bank accounts, obtaining loans, or creating a false identity for organized crime. They will focus on accurately replicating complex features like hologram13s and attempting to alter personal data, such as the photo or date of birth, on a genuine card.
-
Voter Cards: The main threat is election fraud. The goal is not to create a perfect identity, but to enable illegal voting. This often involves mass duplication11 of cards to allow for "ballot stuffing" or enabling single individuals to vote multiple times. Forgers prioritize speed and volume, so the cards may lack finer details, but are good enough to fool a busy poll worker.
-
Social Security Cards: Here, the threat is long-term financial fraud. A forger wants to create a document that can be used for years to illegally claim government benefits. The forgery must be durable and withstand casual, repeated scrutiny over a long period. The financial gain is cumulative, so the effort to create a convincing document is justified.
Understanding these different attack vectors is the first step in designing a truly effective security solution.
What are the Absolute Must-Haves for Secure Document Printing?
Choosing security features can feel overwhelming with hundreds of options available. But picking the wrong ones, or not layering them correctly, wastes money and leaves your documents vulnerable to attack.
The core requirements are simple. You must use customized security materials unavailable to the public, create a multi-layered design2, use a professional security printing process, and include both visible and hidden anti-counterfeiting features for easy verification by anyone.

Over the years, I've seen many clients get lost in the technical jargon of security features. The truth is, a strong document relies on a few core principles, not just one "magic" feature. Think of it as building a fortress. You don't just build one big wall; you build multiple layers of defense. If an attacker gets past the first layer, they are met by a second, and then a third. This layered approach is the key to creating a document that is not only difficult to forge but also easy to authenticate. It’s a philosophy we apply to every government project we undertake.
The Four Pillars of Document Security
These four pillars are non-negotiable for any serious secure document project.
-
Customized Security Materials: The foundation of the card must be secure. This means using materials that are not commercially available. For paper documents like certificates, this could be security paper with custom watermarks and embedded security fibers. For cards, it means using unique PVC or Polycarbonate compositions that are controlled and traceable.
-
Multi-Layered Structural Design: A secure card is not a single piece of plastic. It's a sandwich of different layers fused together. This includes the base material, specialized security printing, a holographic overlay or laminate, and more. Each layer protects the others, and trying to separate them should destroy the card.
-
Professional Security Printing Process: The way the card is printed is a security feature itself. We use techniques that require specialized equipment and expertise, such as Guilloché patterns14 (the fine, intricate lines you see on banknotes), microtext15 that is too small to be read by the naked eye, and color-shifting inks16 (OVI) that change color when tilted.
-
Verifiable Anti-Counterfeiting Features: A document is only secure if its authenticity can be checked. We build in features for different levels of inspection.
| Verification Level | Example Feature | Who Verifies It? |
|---|---|---|
| Level 1: Overt | Hologram, Color-Shifting Ink | General Public, Officials |
| Level 2: Covert | UV Invisible Printing17, Microtext | Border Guards, Police (with tools) |
| Level 3: Forensic | Unique Chemical Taggants, Substrate DNA | Forensic Lab Specialists |
How Do You Ensure a Secure Card Cannot Be Altered or Misused?
A genuine card can still be a major threat if a criminal can alter it. Changing a photo or a name on a real document creates a "partially genuine" forgery that is extremely difficult to detect.
You achieve this through robust tamper resistance. The card must be designed so that any attempt to alter it—like changing a photo or personal data—causes visible, irreversible damage. This physical evidence immediately shows that the document has been compromised.

Think of it like a security seal on a medicine bottle. The goal isn't just to keep the bottle closed, but to give you clear, undeniable proof if someone has tried to open it. We apply this exact same principle to identity documents. A forger's dream is to get a genuine document and just change the one or two details they need. Our job is to make that dream impossible. If they try to peel a layer, change a photo, or erase a name, the card must fight back and destroy itself in the process, leaving behind a scarred, useless piece of plastic.
Making Alteration Impossible
The goal is to make any tampering attempt obvious to even a casual observer. This is achieved through several key strategies that focus on the physical construction of the document.
-
Anti-Tampering Construction: This is about how the card is physically built. For laminated cards, we use adhesives and materials so that trying to peel back the laminate to access the printed information underneath will cause the print to split and delaminate, permanently defacing the card. For high-security polycarbonate cards, the layers are fused together with heat and pressure, without adhesives. They become one solid piece of plastic, so trying to separate the layers will cause the card to crack or shatter.
-
Anti-Modification Features: These features protect the personalized data. One of the best methods is laser engraving18, where the holder's photo and biographical data are burned directly into the card body. This is common in polycarbonate cards. Unlike ink printed on the surface, this engraved data cannot be erased or altered without leaving obvious pits and marks. We also print complex, fine-line security backgrounds over the area where the photo is placed, making it nearly impossible to seamlessly swap a photo.
-
Anti-Reuse Technology: This is more common for single-use documents like tax stamps or visa stickers. These often use tamper-evident materials, such as holographic foils that break apart into a "VOID" pattern if someone tries to peel them off one document to move to another. This ensures the security feature is used only once.
Is a Secure Design Enough, or Does Manufacturing Also Need to Be Secure?
You can design the most perfect, unforgeable card in the world. But what if extra, unauthorized cards are printed? Or if the blank security paper is stolen? The entire project is compromised from the inside.
A secure design is not enough. The manufacturing process itself must be just as secure as the card. This requires a controlled production environment, complete traceability of all materials, data isolation, and strict confidentiality protocols to prevent internal theft, leaks, or unauthorized production.

A document's security chain is only as strong as its weakest link. In many cases, that weak link is not the design, but the production facility. I've heard horror stories from government officials about projects where blank cards or rolls of security laminate "disappeared" from a supplier, only to show up on the black market. This is why our company, Genuine Printing, has built our reputation on trust and control. When a government entrusts us with a project, they are not just buying a product; they are buying a secure process from start to finish. This commitment is why we have been a trusted supplier for government-level projects for over 15 years.
The Secure Factory: A Fortress for Your Documents
Creating a secure manufacturing process means treating the production facility like a bank vault. Every person, every material, and every piece of data is strictly controlled.
-
Controlled Production Environment: Access to our production floors is highly restricted. We use biometric scanners19, 24/7 CCTV surveillance, and secure zones for different stages of production. All waste materials, like misprints or test sheets, are shredded and destroyed on-site under supervision to ensure nothing leaves the facility.
-
Material and Batch Traceability: We implement a strict chain of custody. Every sheet of security paper, every roll of hologram13 film, and every blank card is assigned a unique number and tracked from the moment it enters our warehouse to the moment the finished product is shipped. This allows for a complete audit trail and prevents any material from going missing.
-
Data and Production Isolation: The personal data of citizens is the most sensitive asset. The network we use for personalization and production is physically "air-gapped," meaning it is completely disconnected from the internet and our company's internal office network. This prevents any possibility of a remote data breach.
Conclusion
Securing national documents requires a holistic approach, from understanding specific threats to controlling every step of production. It's about building layers of trust, not just printing a card.
Explore how unique materials enhance the security of ID cards, making them resistant to forgery and unauthorized duplication. ↩
Learn how layering different security features creates a robust defense against tampering and forgery. ↩
Discover the advanced printing techniques that ensure the authenticity and durability of secure documents. ↩
Understand how these features allow easy verification of a document's authenticity by officials and the public. ↩
Find out how these features prevent unauthorized changes to secure documents, maintaining their integrity. ↩
Learn about the importance of tracking materials and processes to prevent internal theft and unauthorized production. ↩
Understand the risks of forged voter cards and their potential to disrupt democratic processes. ↩
Learn how fraudulent social security cards can deplete resources and destabilize welfare programs. ↩
Discover how secure ID cards play a vital role in managing and protecting a nation's identity. ↩
Explore the consequences of identity theft on individuals and national systems, highlighting the need for secure ID cards. ↩
Explore the methods used in election fraud and the importance of secure voter cards to prevent it. ↩
Learn about the strategies used in welfare fraud and the role of secure social security cards in prevention. ↩
Explore the use of holograms as a visible security feature that deters counterfeiting. ↩
Discover how intricate line patterns enhance the security of printed documents, making them hard to replicate. ↩
Find out how tiny text, invisible to the naked eye, adds a layer of security to prevent counterfeiting. ↩
Learn how inks that change color when tilted provide a visual security feature for ID cards. ↩
Understand how invisible printing under UV light adds a covert layer of security to ID cards. ↩
Learn how engraving personal data into the card body prevents alteration and ensures durability. ↩
Discover how biometric technology restricts access to secure facilities, protecting sensitive production processes. ↩
